Thunderbolt drive news
(Note 4/2020, many of the products introduced in 2014 are now out of date in 2020)
Apple has left Firewire and adopted Thunderbolt as their recommended high speed connection for external hard drives (and monitors and other devices). With the Late-2013 “tubular” MacPro, Apple is making it quite explicit that there is no longer any place for drives internally in Macintosh computers. In the mean time Intel has been quietly promoting the inclusion of Thunderbolt into higher end PC motherboards and workstations.
Thunderbolt is a Intel development with cooperation from Apple, which extends the PCI-e bus to an external interface and includes connectivity for DisplayPort graphics signals. The speed that it provides for data transfer is of particular interest to media production professionals (Video editing, music recording, animation) and for scientific, graphic, and other large data set applications. The extension of the PCI-e bus also opens the door for high performance external video and processing acceleration cards such as the Red Rocket, AJA Kona, Black Magic, Bluefish, DeltaCast, Matrox Mojito.
Thunderbolt hard drives and enclosures were slow to come to market but a number of models are now shipping. Thunderbolt products do remain pricey as the chipset adds a premium over the cost of USB 3.0 drives. As chipsets become more common and manufacturers get competitive we should start to see the prices creeping down.
Here is a quick review of what is available as of Oct 15 2014
Firmtek:
The Thundertek/PX-Q6G is a promising development, a Thunderbolt to eSATA solution which actually supports Port Multiplier, for up to 20 external hard drives (in four 5 bay eSATA enclosures). You do have to purchase the Thunderbolt cable and the eSATA enclosures or external drives separately. Unfortunately the Thundertek has only a single Thunderbolt port, making it a terminal device (no daisy chaining) and does not come with the Thunderbolt cable.
The ThunderTek/PX is a Thunderbolt to PCI-e slot external chassis for Macintosh machines with Thunderbolt ports, it can take a PCI-e half-length card. In combination with the SeriTek/Q6G 4-external-port eSATA card, it creates a Thunderbolt to eSATA 4 port solution, the combination is called the Thundertek/PX-Q6G. The ThunderTek/PW version is the same but is PC compatible as well as Mac compatible.

Firmtek ThunderTek/PX
LaCie:
The eSATA Hub Thunderbolt series did ship earlier than most of its competitors, and offers two eSATA ports. Sadly, it is not Port Multiplier compatible, so it supports at most 2 external eSATA drives. It does have two Thunderbolt ports for daisy chaining, which is a plus, but no cable.
CanadaRAM LaCie Thunderbolt series

LaCie eSATAHub Thunderbolt

LaCie eSATAHub TB back
LaCie is shipping their 2Big Thunderbolt external drives, which have 2 x 3.5″ drives in a RAID pair within the Thunderbolt enclosure, these come with the Thunderbolt cable and dual Thunderbolt ports.
CanadaRAM LaCie Thunderbolt series
C

LaCie 2big Thunderbolt
LaCie 2big Thunderbolt Back
The 5Big Thunderbolt has 5 drives in a RAID configuration. These can be configured as a RAID 0, or by using Apple’s Disk Utility, they can be formatted either as RAID 1 mirrored pairs (2 pairs plus one independent drive, or one pair and three independent drives), or as 5 independent drives.
CanadaRAM LaCie Thunderbolt series

LaCie 5big Thunderbolt
The LaCie Little Big Disk Thunderbolt Series is a smaller size desktop drive (requires an AC adapter so it is not considered a mobile drive) available with 2 hard drives in a RAID0 Array or with two SSD drives internally. They have two Thunderbolt connectors and include a cable.
CanadaRAM LaCie Thunderbolt series

LaCie LittleBigDisk Thunderbolt
The LaCie Little Big Disk Thunderbolt2 1 TB SSD is a compact size desktop drive with two 512 GB SSD drives in a RAID 0 Array and two Thunderbolt 2 (20 Gbps) connections, making it one of the fastest currently available drives. Thunderbolt cable is included.
1TB LaCie Little Big Disk Thunderbolt2 SSD 1TB USB3.0 + TBolt Mobile RAID 0 (2X512) SSD drive, fanless with cable up to 1300 MBps RPM External, Thunderbolt 3 Yr Warranty 9000477

LaCie LittleBigDisk Thunderbolt2
The single-drive options are the LaCie d2 USB 3.0 Thunderboltâ„¢ Series, which also have USB 3.0 but sadly have just one Thunderbolt connector. The cable is included.
CanadaRAM LaCie Thunderbolt series

LaCie d2 Thunderbolt
LaCie has some mobile drives, the Rugged USB3 Thunderbolt Series, available with hard drives or SSD drives, encased in bright orange rubber shock resistant material, and including a 1.5 foot Thunderbolt cable but just one Thunderbolt port
CanadaRAM LaCie Thunderbolt series

LaCie Rugged Thunderbolt
Western Digital:
WD is shipping, in limited quantities, their MyBook Thunderbolt Duos which, like the LaCie 2Big, have two drives in the enclosure. Credit to Western Digital for including both the Thunderbolt cable and the second Thunderbolt port for daisy chaining.
CanadaRAM Western Digital Thunderbolt series

Western Digital MyBook Thunderbolt

WD MyBook Thunderbolt open
MyPassport Pro 2 TB and 4TB RAID drives
Portable, bus-powered aluminum external drives with two 2.5″ drives inside, in a RAID 0 configuration, these come in 2 TB and 4 TB sizes, and have maximum data throughput of about 230 MBps. They have a tethered Thunderbolt cable (short), and no daisychaining capability. As far as we know, they are not shipping in Canada as of Aug 6 2014.

HighPoint:
The Highpoint RocketStor 5212 Thunderbolt brings a quick-load dual slot “Disk toaster” to the Thunderbolt arena. This is great for the convenience of swapping 3.5″ and 2.5″ SATA drives in and out. On the downside, Highpoint provides neither a Thunderbolt cable nor a second Thunderbolt port for daisy chaining.
CanadaRAM Highpoint Thunderbolt

Highpoint RocketStor Thunderbolt with 1 2.5″SSD and 1 3.5″ HDD
Highpoint have also released some Thunderbolt2 to Mini-SAS high performance external interface adapters, with Mini-SAS interfaces for enterprise level SAS storage bays (can also be broken out to multiple eSATA connections)
RocketStor 6328 RAID interface with two 20Gb/s Thunderbolt2 Ports, two Mini-SAS Ports and Hardware RAID 0,1,5,6,10,50 and JBOD
RocketStor 6328L interface (no internal RAID) with two 20Gb/s Thunderbolt2 Ports, two Mini-SAS Ports
RocketStor 6324L interface (no internal RAID) with two 20Gb/s Thunderbolt2 Ports, one Mini-SAS Port

Buffalo:
Ministation 1 TB THUNDERBOLT portable Hard Drive HD-PA1.0TU3 Thunderbolt speed in a pocket sized drive, comes with USB 3.0 as well. Overall, it scores highly for portability, the performance will top out at the throughput of the 2.5″ hard drive, which is slower than a desktop 3.5″ drive. The inclusion of neither a Thunderbolt cable nor daisy chain second port is disappointing.

Buffalo Ministation Thunderbolt HD-PA1.0TU3
Buffalo’s Drivestation Mini Thunderbolt SSD is a compact desktop drive which has two SSD drives in a RAID for high speed storage up to 763 MB/s transfer rate. It comes with dual Thunderbolt ports for daisy chaining and a Thunderbolt cable.

Buffalo Drivestation Mini Thunderbolt SSD

Buffalo Drivestation Mini TB back
Data Robotics:
DROBO 5D – 5 Bay Storage Array is one of the few devices that comes with both USB3.0 and Thunderbolt ports, it has room for up to 5 3.5″ drives plus a unique approach – an mSATA slot accessible from the bottom of the drive, for an mSATA SSD drive; this is intended for cache memory, which could speed up the RAID performance.
It is an expensive solution that uses a proprietary RAID system internally.

Drobo 5d Thunderbolt

Drobo 5d back
Drobo Mini: four bay 2.5″ drive enclosure, Two Thunderbolt and one USB 3.0 port. No Thunderbolt cable. mSATA slot in the Drobo Accelerator Bay for a caching SSD drive (optional).

CanadaRAM Drobo Mini link
Kanex:
Kanex has a line of Thunderbolt adapters, one for SATA and USB 3.0 (useable simultaneously) and one for USB 3.0 and Ethernet (intended for MacBook Airs which don’t have an RJ-45 port)
Canadaram Kanex Thunderbolt to USB3.0 + eSATA Adapter KTU10


Cables
Canadaram 1M Kanex Thunderbolt 1 m. cable M-M TBOLT1M
Canadaram 2M Kanex Thunderbolt 2 m. cable M-M TBOLT2M
Seagate:
Backup Plus for Mac with Thunderbolt external single-mechanism 3TB desktop drive includes both a cable and a daisy chaining second Thunderbolt port.
CanadaRAM 3TB Backup Plus for Mac with Thunderbolt STCB3000400 Link

Seagate Backup Plus STCB3000400
Seagate also has adapters to convet GoFlex and Backup Plus drives purchased originally with USB or Firewire interfaces to Thunderbolt. The adapters are specific to certain models.|
Portable Thunderbolt Adapter for Backup Plus Portable STAE128 for mobile Backup Plus 2.5″ drives (Thunderbolt cable not included)
Desktop Thunderbolt Adapter for Backup Plus STAE129 for desktop Backup Plus 3.5″ drives (Thunderbolt cable not included)
Thunderbolt Adapter for GoFlex drives STAE121 (Thunderbolt cable not included) Intended as a Thunderbolt adapter for GoFlex Ultra-Portable portable drives with detachable adapters. The GoFlex Slim drives are too thin and they are loose when fitted, possibly leading to SATA connection failure. This item may be discontinued, it seems to have disappeared from most catalogs.

Sonnet:
Sonnet has their own take on an external PCI-e chassis, Echo Express III-D Desktop Thunderbolt 2 Expansion Chassis, which is a three-slot PCI-e chassis, and has support for Thunderbolt 2 (20 Gbps). The Echo Express III-R Rackmount Thunderbolt 2 Expansion Chassis is a rack-mount version of the same.

Sonnet Echo Express 3d
The Echo Express SE II Thunderbolt 2 Expansion Chassis is similar but with two half-length PCI-e slots

Their latest entry is the Echo Express SEL Thunderbolt 2 single slot expansion chassis, which accommodates one low profile PCI-e card only.

The xMac Mini Server is a unique rackmount product that houses a Mac Mini, adds two PCI-e slot and a 150W power supply so the Mini can run higher end video editing cards.
Keep in mind that with this and any other expansion chassis, support for PCI-e cards will be limited to those cards which are on the manufacturer’s supported list.
Next up is the fabled Echo 15 Thunderbolt Dock 15-port docking station for computers with a Thunderbolt port. This should be intriguing when the products actually ship – an optical drive and a internal hard drive, plus other ports, this would seem to be a solution made for Macs that ship without optical drives. We are told the first units of these will start arriving in September 2014 after a close to two years wait on backorder. I’m sorry, Sonnet but credibility suffers when you continually announce ship dates only to push them back each time.
4 x USB 3.0 ports, 1 internal SATA and 1 external eSATA ports, 1 FireWire 800 port, Gigabit Ethernet, and audio interfaces, plus a second Thunderbolt port for daisy chaining. Includes either 8x DVD±RW drive or, optionally, a Blu-ray BD-ROM/8x DVD±RW drive. Supports installation of one 2.5″ or 3.5″ SATA internal hard drive or SSD (and is available with various drive configurations pre-installed).
The Echo 15 Pro+Thunderbolt Dock 16-port comes with a Blu-Ray drive pre-installed, and it has connections for either two 2.5″ drives or one 3.5″ drive internally.

Sonnet Echo 15 Thunderbolt Dock
Promise:
Promise has several variations of the Pegasus line of Thunderbolt enclosures.
The Pegasus J4 is a 4 bay 2.5″ SATA RAID enclosure that can hold laptop 2.5″ SATA hard drives (9.5mm or 7mm tall) or 2.5″ SATA SSDs. It will create a RAID array out of the drives, allowing up to 750 MB/sec transfer with SSDs. It does have two Thunderbolt ports but does not come with the cable. With SSDs, the J4 can create an extremely fast RAAD drive in a portable package.
CanadaRAM Promise Thunderbolt series

Promise Pegasus J4
Pegasus R4 and R6 are the 4-bay and 6-bay high performance hardware RAID Solutions with two Thunderbolt 10 Gbs ports. They are available in a variety of hard drive configurations up to 24 TB.

Promise Pegasus R4 and R6
The Pegasus2 line is Thunderbolt 2 enabled hardware RAID storage with 4, 6 or 8 drive bays and up to 32 TB of storage per tower. Promise is pitching the Pegasus2 line toward video and multimedia production, giving performance fast enough for 3D and 4K video editing together with enterprise level RAID protection.

Promise Pegasus2 family
The Promise SANLink and SANLink2 are Thunderbolt external adapters that provide dual 4G Fibre Channel connectivity for Macs for connection to high speed storage area networks in enterprises and video production suites. They have dual Thunderbolt ports for daisy chaining, the SANLink2 supports Thunderbolt2.

Promise SanLink2 External Fibre Channel adapter
OWC:
Mercury Elite Pro Dual USB 3.0 & Thunderbolt RAID Storage Enclosure. Two 3.5″ SATA drive bays. Built in RAID controller supports RAID modes 0, 1, spanning & independent drives. Thunderbolt cable included, two Thunderbolt ports for daisy chaining.
With no drives (add your own) Elite Pro Dual METB7DK0GB Link
With 2 x 2 TB drives Elite Pro Dual METB7DH2.0T
With 2 x 3 TB drives Elite Pro Dual METB7DH6.0T
With 2 x 4 TB drives Elite Pro Dual METB7DH8.0T

OWC Elite Pro Dual Thunderbolt
ThunderBay IV four bay Thunderbolt enclosure. Independent drives or a variety of RAID modes. Note that this enclosure uses software RAID, not a hardware RAID controller in the case. Can take a mixture of hard drives and SSD drives. Two Thunderbolt ports for daisy chaining.
With no drives (add your own) ThunderBay IV TBIVKIT0GB Link
4 x 1 TB drives ThunderBay IV TBIVT04.0S
4 x 2 TB drives ThunderBay IV TBIVT08.0S
4 x 3 TB drives ThunderBay IV TBIVT12.0S
4 x 4 TB drives ThunderBay IV TBIVT16.0S
4 x 120 GB SSD ThunderBay IV TBIVSSD480
4 x 240 GB SSD ThunderBay IV TBIVSSDT1.0
4 x 480 GB SSD ThunderBay IV TBIVSSDT2.0
4 x 960 GB SSD ThunderBay IV TBIVSSDT4.0

OWC ThunderBay IV
Mercury On-The-Go Pro Thunderbolt portable 1 TB hard drive MOTGTBH5T1.0, single Thunderbolt port, so no daisy-chaining, and an odd choice of a slower HDD, I would have thought a Hybrid SSHD or a 7200 RPM HDD would have been better.

Mercury Helios Thunderbolt PCIe Expansion Chassis supports one PCI-e 2.0 half-length PCI-e x1, x4 or x8 card. Two Thunderbolt ports

OWC Helios Thunderbolt PCI-e Chassis
One Stop Systems
One Stop Systems has announced the CUBE line of Thunderbolt/PCI-e expansion chassis
The CUBE family includes
nanoCUBE, which takes one 7.3 inch PCIe short card

The Micro Cube family µCUBE (1 slot), µCUBE2 (3 slot), and µCUBE3 (5 slots) supporting 9.5 inch PCIe short cards

The Cube family CUBE (2 slot), CUBE2 (5 slots), and CUBE3 (8 slots) supporting full-length PCIe cards

The details are important, so make sure you go back to their website check the compatibility list for cards that can be used in the expansion chassis as they are tested.
CalDigit:
CalDigit has a fairly unique enclosure, the CalDigit T3 which is a three-bay Thunderbolt enclosure with quick-swap trays. With three drive bays, it can implement a RAID 0 or a RAID 1 across three drives. With a RAID 1 mirror, that means you have three copies of the data instead of the conventional 2 with a 2 bay RAID. Alternatively, you can have a 2 disk RAID and assign the third bay to be an independent disk (JBOD). This opens up the possibility of a 2 drive RAID 0 for speed, which you could set up some cloning software to periodically copy to a large, slower drive in bay 3 as a backup. Or, two large hard drives for archival data and an SSD for speed on your current working files. SSDs and hard disks can be mixed in this enclosure. It has 2 Thunderbolt ports but no Thunderbolt cable.
CalDigit announced (Oct 20 2014) a Thunderbolt2 version of the T3, and they have increased the warranty to 5 years. It supports hard drives up to 5 TB for a 15 TB maximum capacity and a 1,100 Mbps throughput with SSDs.
A T4 model with four drive bays is announced but not shipping yet

CalDigit T3 RAID Thunderbolt Enclosure
The CalDigit Thunderboltâ„¢ Station is an external Thunderbolt adapter that adds USB 3.0, Audio In & Out, HDMI, and Ethernet connectivity via dual Thunderboltâ„¢ ports. Although the Audio in and out may be a benefit to new MacPro owners, the video and Ethernet ports seem to be aimed at MacBook Air owners. It has neither eSATA nor Firewire outputs, CalDigit is suggesting that the USB 3.0 ports are fast enough for hard drives, and position their AV Pro USB 3.0 and USB 3.0/Firewire 800 enclosures as companions for the Thunderbolt station. The AV Pro enclosures share the same drive caddies as the T3 RAID enclosure, so drives can be interchangeable between them (limited by the RAID configuaration of course).

CalDigit Thunderbolt Station adapter

CalDigit AVPro USB 3.0 / USB3/Firewire 800 enclosure
Belkin:
Belkin has their Thunderbolt Express Dock which provides a Thunderbolt adapter providing 3x USB 3.0 ports, 1x Firewire 800 port, Audio I/O and Gigabit LAN. It provides USB charging power (500 mA only) on the USB ports, has a second Thunderbolt port for daisy chaining, and includes an AC power adapter. Comes in two versions, with and without Thunderbolt cable.

Belkin Thunderbolt Express Dock (rear)
Matrox:
Matrox offers the DS1 Thunderbolt Dock in either a DVI or HDMI versions. This is intended mainly for offering display, audio and Ethernet connectivity for MacBook and MacBook Air machines. It has 2 x USB 2.0 and 1 x USB 3.0 ports, which seems to be a missed opportunity for additional USB 3.0 connections for drives. It oddly puts the microphone and headphone connectors on the back panel. Without a cable, and without a daisy chaining second Thunderbolt port, it does not compare as well against the CalDigit and Belkin offerings.
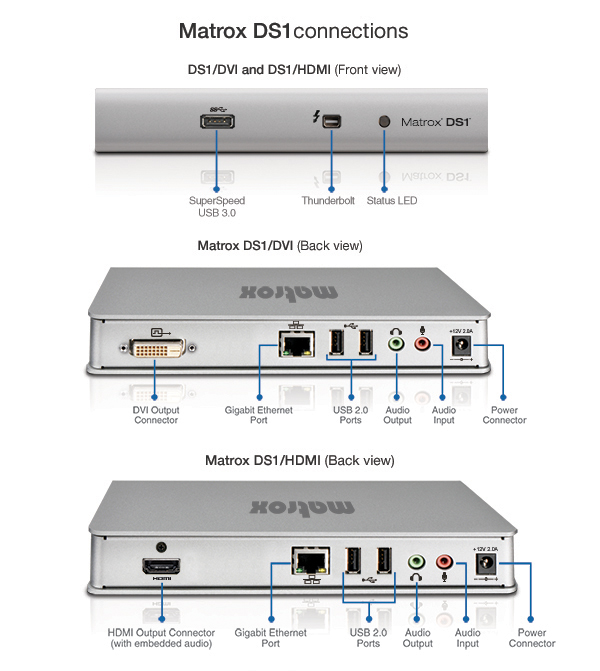
Matrox DS1 dock
Atto:
Atto’s ThunderLink adapters convert from Thunderbolt to various media. They all have 2 x Thunderbolt ports, and come in four versions,

Atto Thunderlink
ThunderLink FC 1082 Two Thunderbolt ports to 2 x 8 Gbps FibreChannel ports,
ThunderLink SH 1068 Two Thunderbolt ports to 8xSATA/SAS, on SFF-8088 port(breakout cable required for connection to SATA or SAS drives)

Atto Thunderlink SH-1068 Back
ThunderLink NT 1102 (10GBASE-T) 10Gb Ethernet on Twisted pair
ThunderLink NS 1101 (SFP+) 10Gb Ethernet with optical LC SFP+
ThunderStream RAID controllers
ThunderStream SC 3808D has 8 x SATA/SAS ports and is an external Thunderbolt to SAS/SATA RAID adapter, connecting MacPros, iMacs and laptops to 6Gb/s SAS/SATA RAID storage devices. The difference between this and the ThunderLink SH 1068 is the addition of an Atto hardware RAID controller. It uses a SFF-8088 connector which can be attached to SAS storage devices with this connector, or SATA devices with an appropriate breakout cable.

Atto Thunderstream Back
G-Technology (HGST a division of Western Digital):
G-Dock EV with Thunderbolt: Two bay dock for 2.5″ drives in G-Drive EV cartridges. The individual cartridges can be used as stand-alone USB 3.0 drives. The G-Dock EV however has only Thunderbolt connectors, not USB or eSATA (despite the specs on the website). Two Thunderbolt connectors allow daisy chaining, Thunderbolt cable included. 2 TB model (2 x 1 TB G-Drive EV drives included)

G-Technology GDock EV Front

G-Technology GDock EV Back

G-Technology G-Drive EV Front

G-Technology GDrive EV Back
G-Raid with Thunderbolt: Dual drive RAID enclosures with either 4 TB (2x2TB)or 8 TB (2x4TB) 3.5″ 7200 RPM Drives. Two Thunderbolt connectors allow daisy chaining, Thunderbolt cable included.

G-Technology GRaid Front

G-Technology GRaid Back
G-Drive Pro with Thunderbolt: Single drive, 2 TB or 4 TB 7200 RPM hard drive. Includes a cooling fan for more reliable 24/7 operation but may increase noise level for recording studios and other quiet environments. USB 3.0 connection, but disappointingly for a drive labelled “Pro” only one Thunderbolt port, so no daisy chaining is possible. Thunderbolt cable is included, three year warranty.

G-Technology GDrive Pro Front

G-Technology GDrive Pro Back
G-Drive Mobile with Thunderbolt: Mobile 2.5″ hard drive with one Thunderbolt port and one USB 3.0 port. No daisy chaining. 1 TB model, three year warranty.

G-Technology GDrive Mobile Back
G-SPEED Studio 4 bay RAID, two Thunderbolt 2 ports, comes with Thunderbolt cable. available in 12TB, 16TB and 24TB configurations, from US$2200 to US$3600

G-Drive with Thunderbolt: Single drive, 3 TB or 4 TB 7200 RPM hard drive. USB 3.0 connection, only one Thunderbolt port, no daisy chaining. Thunderbolt cable is included, three year warranty.

Areca
Areca from Taiwan has some Thunderbolt and Thunderbolt 2 RAID towers. Some of the models include out of band RAID management capability through the LAN port.
ARC-8050T2 Thunderbolt 2 to 6Gb/s SAS 8 – bay RAID Storage (note: for Serial Attached SCSI drives only)

Areca 8 bay SAS RAID ARC-8050T2 Thunderbolt 2
ARC-8050 Thunderbolt to 6Gb/s SAS 8 – bay RAID Storage (note: for Serial Attached SCSI drives only)
ARC-5028T2 Thunderbolt 2/USB 3.0 to 6Gb/s SATA 6 – bay RAID Storage

Areca 6 bay RAID ARC-5028T2 Thunderbolt 2
ARC-5026 Thunderbolt/USB 3.0 to 6Gb/s SATA 4 – bay RAID Storage

Areca ARC-5026 4 bay SATA TB1
That’s all the news we have for now, more updates as things progress.
Like this:
Like Loading...









































































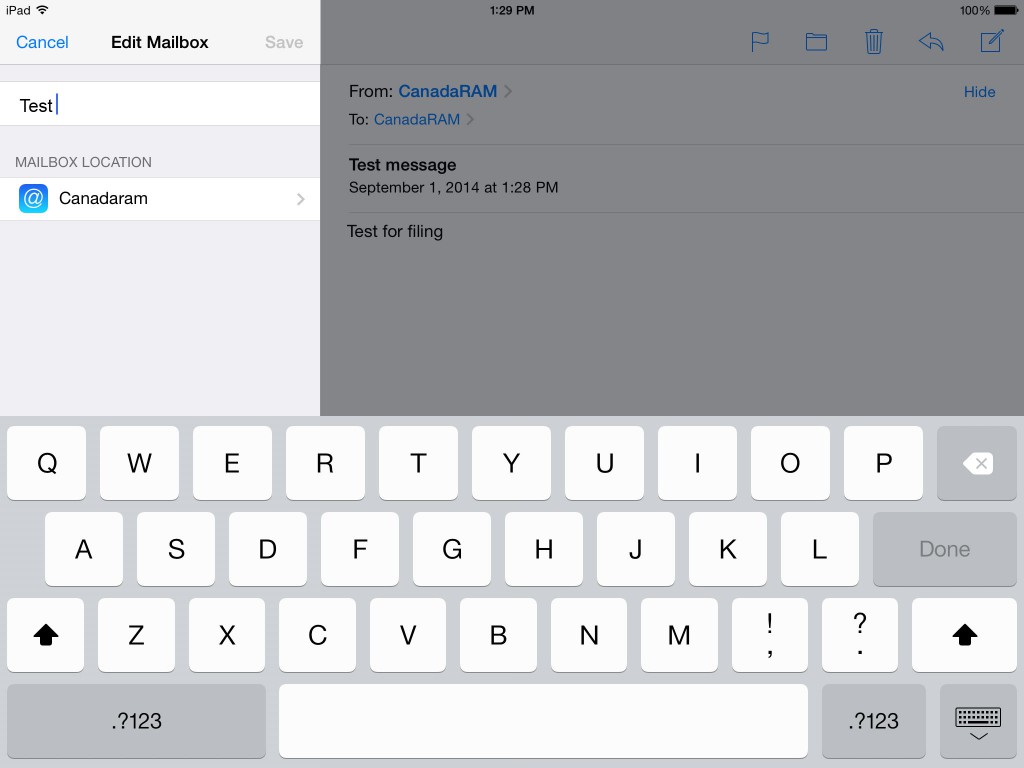
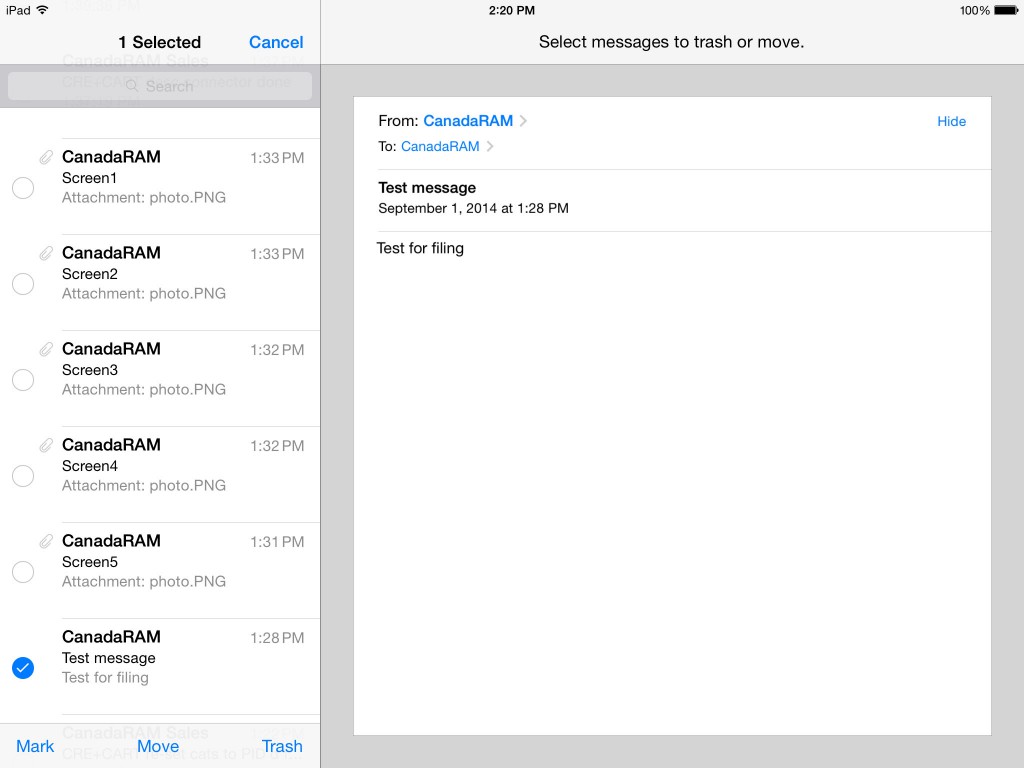
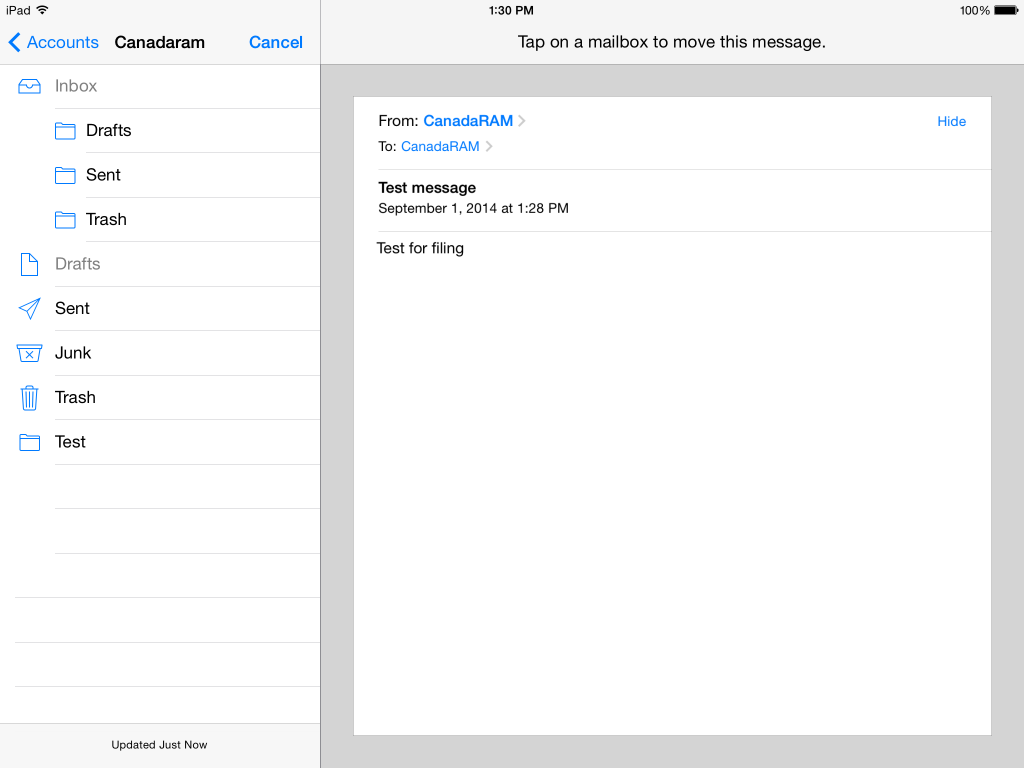





 Web browsing is full of hazards. Even reputable websites can have poisoned banner ads from third parties, which can attempt to hack your machine or browser settings. You don’t even have to click on a “bad” website to be the victim of a “drive-by download”. Some browsers such as Internet Explorer have a long history of vulnerabilities, and scripting languages such as JavaScript and ActiveX, Java, and media playing programs like Flash are all vectors for malware.
Web browsing is full of hazards. Even reputable websites can have poisoned banner ads from third parties, which can attempt to hack your machine or browser settings. You don’t even have to click on a “bad” website to be the victim of a “drive-by download”. Some browsers such as Internet Explorer have a long history of vulnerabilities, and scripting languages such as JavaScript and ActiveX, Java, and media playing programs like Flash are all vectors for malware.



Event: DesertBus For Hope Charity drive
DesertBus 2014 is now in progress, http://desertbus.org/
My friends from the Loading Ready Run sketch comedy troupe in Victoria are playing the most boring video game ever made (Penn & Teller’s DesertBus*) to raise money for the Child’s Play charity. They will keep driving the DesertBus 24/7 for as long as people donate to the charity. While they are driving the bus, they hold auctions, do skits and songs for donations, and accept challenges to do hilarious and/or embarrassing things for donations.
The volunteer drivers have over 160 hours to drive the DesertBus (keep them driving by donating, the more money raised, the longer they are tortured by having to play the worst-game-in-the-world.)
DesertBus for Hope has passed $400,000 on this years campaign so far, and have raised over 2 million for charity since 2007
Tune in and support the gang and the Child’s Play charity, which provides toys and games to children who are seriously ill and in hospital.
* Developed by comedians Penn and Teller, the “anti-game” DesertBus is a first-person driving game, where you drive a bus from Tuscon to Las Vegas, in real time. The road is dead straight, and — nothing happens. Then when you reach Las Vegas 4.5 hours later, you —turn around and go back. The bus’ steering is defective, so if you don’t pay attention it will veer off the road and crash. At which point a tow truck is dispatched to tow you back — in real time.
Here’s an article from last year in the New Yorker about their effort http://www.newyorker.com/tech/elements/desert-bus-the-very-worst-video-game-ever-created
Share this:
Like this: