Updated August 27 2012
Computerworld has published an article about new Java based malware which can infect Mac, Windows and Linux machines through a vulnerability in Oracle’s Java 7.
OSX 10.7 and OSX 10.8 come with Java disabled by default, so you are safe unless you have installed it.
Mac OSX 10.6 and earlier have Java enabled in the default configuration so you are at risk if you have it still enabled and have Java Runtime Environment 1.7
The first line of defense is to DISABLE JAVA.
Either Globally:
Go to Applications > Utilities > Java Preferences and turn it off,
or
“Go to Folder” from the Finder’s “Go” menu, enter
“/Library/Java/JavaVirtualMachines/”
and drag the file “1.7.0.jdk” into the Trash.
or, within each of your web browsers:
Safari: click Preferences, then Security tab uncheck “Enable Javaâ€.
Also uncheck the “Open ‘safe’ files after downloading†box in Safari Preferences > General tab.
Google Chrome: open Preferences, type “Java†in the search text box. Scroll down until you reach Plug-ins, click “Disable individual plug-ins.†If Java is installed, you’ll see a “disable†link for it.
Firefox: While in Firefox, from the top menu, choose Tools, Add-ons, disable the Java plugin(s)
www.maclife.com/article/howtos/how_disable_java_your_mac_web_browser
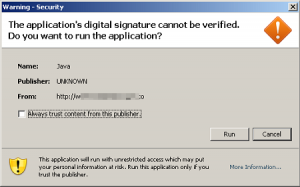
The exploit is apparently usable by malware as a “drive-by download” which could be launched by a poisoned website. On a Mac it will pop up a message asking permission to download Java software from Oracle. Make it a policy to never let an installer or website download and install Java.
July 2012
Another Trojan horse program has been discovered that uses the Java language to insert spyware on multiple operating systems including Macintosh OSX. F-Secure Blog Post
The trojan horse is contained in a Java Applet which attempts to install when you visit a compromised website. The first website was identified as a Colombian Transport site. It attempts to install a back-door program on the machine which would allow the malware writers to view and copy the contents of the machine or control it remotely.
There are two lines of defense:
First, never download or install any program that you do not know 100% for sure is reliable. Do not proceed with an install that says the source is untrusted or the security certificate is invalid. Trojans like these rely on ‘social engineering’ to trick you into installing them and bypassing your machine’s security.
Second, consider disabling Java in your browsers, because it is a vector for viruses – it allows programs to run in your browser which can modify your drive and system. Not many people require Java for day to day use, if you have a web application that requires Java and you have turned it off, the web page will inform you that Java is required.
- In Internet Explorer, go to Tools: Internet Options: Advanced and uncheck the Sun Java add-in
- In Firefox, go to the Firefox or Tools menu, choose Add-ons: Add-Ons Manager; PlugIns, select the Java Platform item and click Disable
- In Chrome you can either block plug-ins, which allows you to permit them to run selectively, or you can disable plug ins, which stops them permanently. To disable Java, go to the Plug-ins page by typing in your Location bar chrome://plugins/. Find the Java plug-in and click Disable.
Note: Java and JavaScript are two different things, and not related in any way. JavaScript is required for many web page features to work. For both Windows and Mac you can control which JavaScripts run on a specific web page by using Firefox as your browser and installing the NoScript extension
Mac OSX:
This trojan requires legacy PowerPC software components, so OSX 10.7 Lion and the upcoming Mountain Lion are safe, as there is no support for Rosetta, which runs the legacy PowerPC code. OSX 10.6.x made the Rosetta install optional, so it is not at risk unless Rosetta had been installed to run older programs. Do not authorize Rosetta to install if you are prompted for it and are not installing a known program.
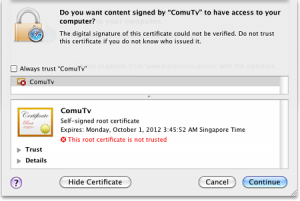 For OSX 10.5.x and earlier, Rosetta is on by default and the trojan masquerades as a program that must be downloaded to the Mac. The user has to issue permission for it to install, and the OSX installer warns that it is from an untrusted source.
For OSX 10.5.x and earlier, Rosetta is on by default and the trojan masquerades as a program that must be downloaded to the Mac. The user has to issue permission for it to install, and the OSX installer warns that it is from an untrusted source.
If you followed the instructions from the Java trojan warning in April, you will have turned off Java in your browsers already. If you have not, do so now. Most individuals do not need the ability to execute Java programs, and turning Java off removes this vector for malware.
Make sure that your Apple Software Updates are current, and if you must run Java, Sun had announced that you will be able to get the Macintosh Java software updates directly as well.

Pingback: Zero Day Java Exploit – Disable Java Now | CanadaRAM: Memory and Computer Q&A
Pingback: Q. Is there any Internet security threat if I only visit reputable sites? | CanadaRAM: Memory and Computer Q&A