Microsoft’s Internet Explorer Web browser has been exposed to have a vulnerability that hackers have been exploiting — before Microsoft has had a chance to respond with a patch. (this is the meaning of the term Zero Day, a hole that is open for exploitation before it is recognized and remediated).
The details of the vulnerability aren’t very important, more important is the fact that there is nothing protecting you if you accidentally visit a website poisoned with the code to leverage the vulnerability of the Internet Explorer browser.
A commentator on Canada.com helpfully suggests that computer users should avoid going to such pages: “you, as a browser of the internet, have to actually choose to go to a malicious web page. Don’t make that choice and you’ll be fine.”
o.canada.com/technology/internet/microsoft-works-to-patch-latest-hole-in-web-security
Hello? I am sure that malware writers are not going to advertise on the page that “this is a launch pad” for the exploit. The exploit can be launched by a drive-by download from a booby trapped website, no click needed. I help people every day who are fooled into going to web links on pages, popups and web advertisements that then install whatever the author wants. So saying “just don’t go there” isn’t very helpful.
The correct response is to not use Internet Explorer. Ever again.
Mac owners went through Internet Explorer withdrawal several years ago and survived quite well, now it is time for Windows users to do the same…Especially if you are running XP, because your OS and Internet Explorer have been orphaned by Microsoft and they have no obligation to release any security patches for you, even in the face of known vulnerabilities.
Delete your Internet Explorer shortcuts and set your Default Web Browser to be Firefox. Download the latest Firefox for your particular operating system here. At the same time, install the NoScript extension to Firefox, which will prevent websites from running Javascript, Java, or automatically playing media files such as Flash (all of these have been used as vectors for malware and trojan horses).
Get NoScript here addons.mozilla.org/en-US/firefox/addon/noscript/
(unfortunately the NoScript home page itself does have advertising on it for potentially unwanted programs (PUPs) so I don’t recommend it.)
Since NoScript blocks all scripts from running, it will make some sites that you want to go to look different or not work well. The solution to this is to look at the yellow bar that NoScript puts on your browser (or click on the S icon), informing you which web domains are trying to run scripts when you visit the page. You then have the choice of which domains you will permit scripts to run, and you can permit one time only, or permit a trusted site to run scripts permanently. It’s useful to know that when you visit your favorite sites, what other advertisers and tracking sites are active in the background, so you can selectively block them.
The general rule is, permit the site you know you are visiting (say, ford.ca) and block outside sites (google-analytics.com, doubleclick.net, admt.com and anything else that may be riding along). If the site requires some content from a different server, you’ll notice something is missing on the page, and you can grant permission to the server that’s needed to make it work.
One thing you will enjoy is a lack of ads and popups on the sites you visit.
Similarly, if a YouTube or Flash video doesn’t run, you can grant permission temporarily for that item or permanently.
More info on NoScript krebsonsecurity.com/tag/noscript/
Video from CNet www.youtube.com/watch?v=GzBqnLgOzwM
Google Chrome does have some tools for blocking scripts as well, but they are harder to get to and harder to control as you are browsing. One would think that Google doesn’t want you to block Google ads and tracking. There are third party script blockers which I have not tested, so can’t vouch for: httpswitchboard, ScriptSafe, ScriptBlock – you can find them at the Google Webstore https://chrome.google.com/webstore/
One thing about Chrome I don’t like is how search redirectors and other malware can reinstall themselves via an Enterprise Policy – this means you can kill it as many times as you like, and like a zombie it keeps coming back. Deleting the policy means digging into Microsoft’s hidden folders and deleting files with names like fk24jfhlwba83nfdkaldnb
Here are two links with details for removal:
www.technipages.com/google-chrome-solve-this-extension-is-managed-and-cannot-be-removed-or-disabled
malwaretips.com/blogs/installed-enterprise-policy-removal/



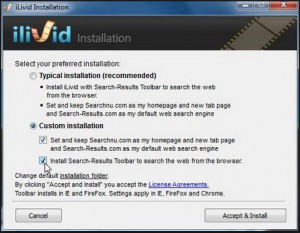
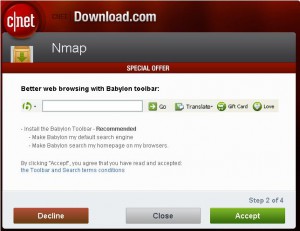 Also make sure also that you Uncheck each of the option checkboxes that suggest “also install….” (some of the companies are getting really cute and reversing this, making you CHECK the box if you DON’T want to install the add ons.)
Also make sure also that you Uncheck each of the option checkboxes that suggest “also install….” (some of the companies are getting really cute and reversing this, making you CHECK the box if you DON’T want to install the add ons.)