Online criminals continue with phishing expeditions. Phishing is sending phony emails that mimic legitimate emails from reputable sources, hoping to get you to click on them to download malware, or to steal your login and password when you arrive at what you think is the real website (but is a simulation of the login page hosted on the criminal’s servers).
The one last week is pretty amateurish
The obvious grammatical errors and the mistake of using a font for the Apple logo show it up. Where is could work is that so many people use iTunes, that a fair number of them will have had password problems in the past few days, so it jumps over the barrier of implausibility for those people. When you see something expected, human nature is to not look at it closely.
But not all phishing attempts are so easy to spot, some are excellent reproductions of courier delivery notices, bank money transfers, invoices from suppliers, etc.
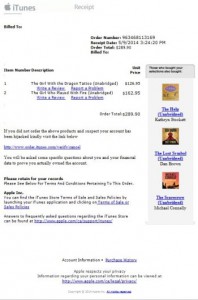
Today’s iTunes phishing attempt is an invoice for a movie rental for an absurd amount and an inviting link saying “Click here to report problems”. This one is better crafted, they managed to make it look like it was coming from Itunes, but from the UK in my case.
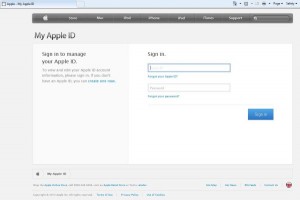
If you click on it, it goes to a fake Apple login page where your ID and password will be stolen
Of course, you can be worried about the criminals making purchases from your Apple account, which you probably have attached to a charge card, so they can ring up hundreds or thousands of dollars of goods. But your Apple ID may allow them to hijack your iPhone or iPad, and because people tend to use the same passwords over and over, they can try out breaking into your email or other online accounts.
The first step is to treat every email that instructs you to click on something with severe prejudice. Even if your bank does want you to log in to them, you should always type in the bank URL in your browser, not click on a link.
Increasingly, banks and other security conscious organization are adopting policies of never including direct links in emails, and always including some confirming information in their emails, such as “Dear Stephen Jones” rather than “Dear Customer”. Apple’s emails always have your real first and last name, and the Apple ID account address.
The second step is to look critically at the contents and the addressing of the email.
In the case of the “Apple iTunes” email, even if the layout, spelling and grammar were perfect, the first thing I spotted is that it was sent to the wrong email address, an email I do not have associated with my iTunes account.
I am an advocate of creating different email accounts for different purposes (this is especially easy if you own your own domain name and can create mail forwarding tables for different mail accounts). Besides making it easier to spot fakes, if I get tired of hearing from xyz company, I can simply delete the mail forwarding rule for the account I created.
Looking at the contents, I see that it has an address in Luxembourg. While Apple Europe may operate out of that country, there is no chance that they would use that address to message me in Canada.
Viewing the headers of the email, the mail was sent from the server xtra.xtrazon.com, not from a server at Apple, and the return path was xtrazon.com. This tells me that the criminals are pretty unsophisticated, because with a little effort they could have forged mail headers to make it at least appear that it came from an Apple server. So you can’t 100% rely on the mail headers to prove it is real, but an off-target header if pretty good proof that it is fake.
Complicating this is that companies will use commercial server farms like Akamai, or will contract their email to ConstantContact or MailChimp or another sending service, so it is a matter of experience, or Google-search skills, to help decide what is legitimate.
The third step – if you find yourself at a login page to a site, and have any doubts how you got there, just quit the web browser without typing in anything. Then when you reopen the browser, type in the URL manually to make sure you get to the real site.
Carefully check the URL of the web page you are on in the browser’s Location bar. Criminals will make up domains that look like a real domain at first glance, like app1e.com or gooogle.com, they will use substitute characters, or embed legitimate sounding names in a phony URL – like itunes.update.co – that goes to update.co in the South American nation of Columbia not to itunes.com or to update.com
And finally, we always recommend using a web browser with enhanced security features, like Firefox with NoScript and with security features turned up.